|
ED-SSL Visibility Appliance
HTTPS network links come closer with life and work since there are versatile cyber applications within IT environment of government and enterprise. After Google provided extensive HTTPS service in 2005, the other content service providers such as Facebook, Twitter, and Yahoo Mail and so on also followed with HTTPS to protect content data.
Extensive HTTPS service also brings the favorite environment for cybercrimes to hide malice ware inside encrypted traffic in order to escape from antivirus system and intrude into enterprise networks. By the data in 2016, incidents of encrypted attack through TLS/SSL rise 60 times compared to 2014, and 29K kind of malice troy agents infect victim systems through TLS/SSL traffic.
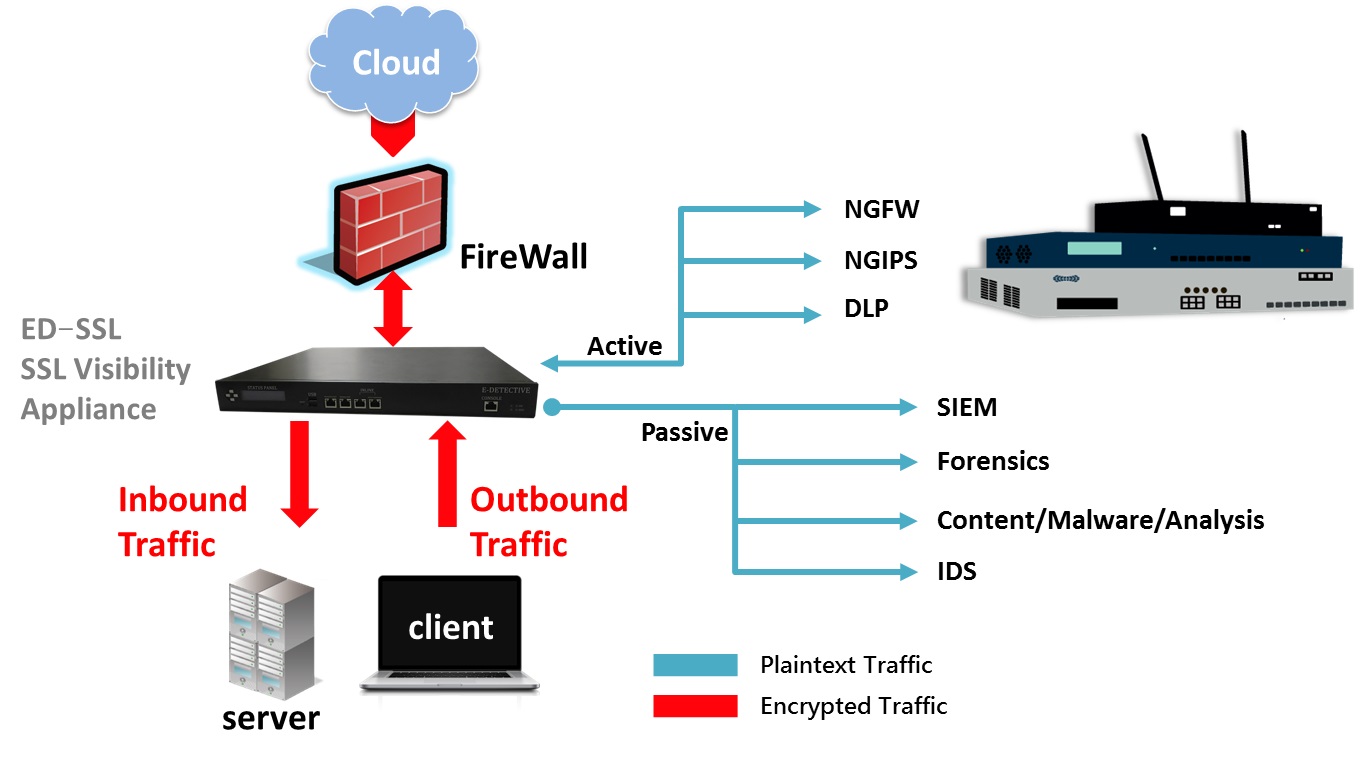
- High TLS/SSL traffic visibility and coordinated work with backend security analysis tools
- Single unified platform for TLS/SSL traffic examination on the agile appliance hardware for potential risk mitigation
- Deployed as upstream proxy to monitor all links without any impact on the functionality and performance of the existing proxy server
- Centralized TLS/SSL handling management and bundled HTTPS visibility capability into enterprise security fundamental platform
- Dynamic linking service by secured deployment strategy in order to reduce management cost and utilize all security resources
- Affordable price with the best price/performance for enterprise and less potential TLS/SSL traffic risk
 SSL Visibility Appliance SSL Visibility Appliance
| Performance |
Specifications |
| Total Packet Processing Capability |
100 MBps |
Configurations |
Network Interfaces: Fixed 3 x 1 Gbps RJ45 |
| SSL Inspection Throughput |
70 MBps |
Power Supplies |
1 x 150W |
| Cut-through Latency |
<40μs |
Management Interfaces |
1x RJ45 |
| Concurrent SSL Flow States |
8,000 |
Operating Temperature |
5°C to 40°C |
| New Full Handshake SSL Sessions |
1,000 per second |
Storage Temperature |
-10°C to 60°C |
| SSL Session Log Entries |
by order |
Dimensions (in.) H x W x D |
1.75 x 8 x 12.75 |
| Encryption |
TLS 1.0, TLS 1.1, TLS 1.2, SSL3, partial SSL2 |
|
| Public Key Algorithms |
RSA, DHE, ECDHE |
| Symmetrical Key Algorithms |
AES, AES-GCM, 3DES, DES, RC4, ChaCha20-Poly1305, Camellia |
| Hashing Algorithms |
MD5, SHA-1, SHA-2, SHA256, SHA384 |
| RSA Keys |
512 to 8192 bits |
| Reliability |
Hardware bypass |
|